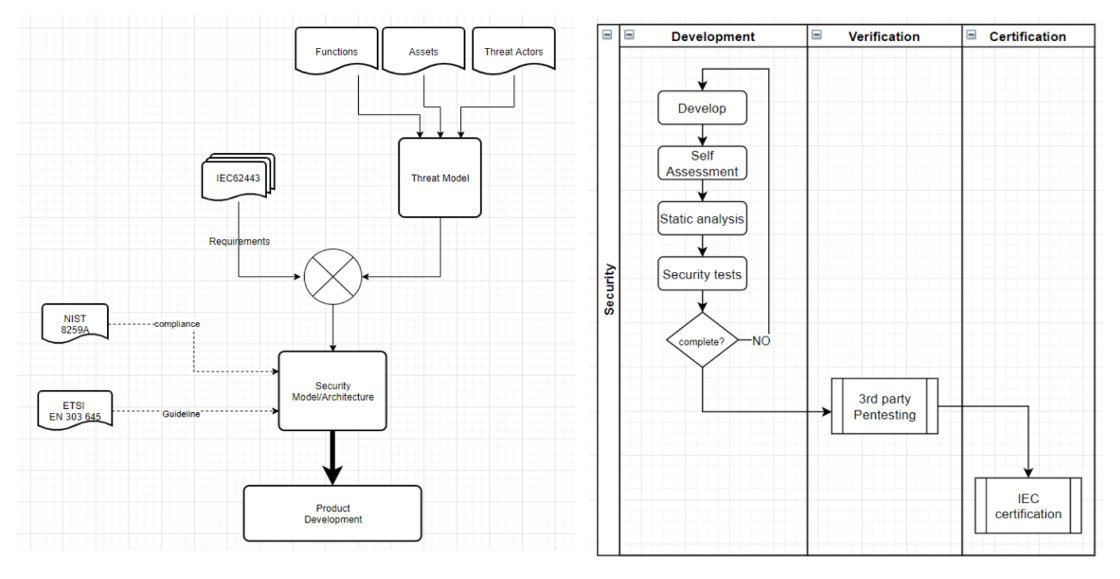
Danfoss Electronic Controllers is following secure development towards IEC-62443 in their Development Teams
Recommendations for Customers
To help keeping your Danfoss products secure and protected, we recommend that you implement below cybersecurity best practices.
Following these recommendations may help significantly reduce your company’s cybersecurity risk.
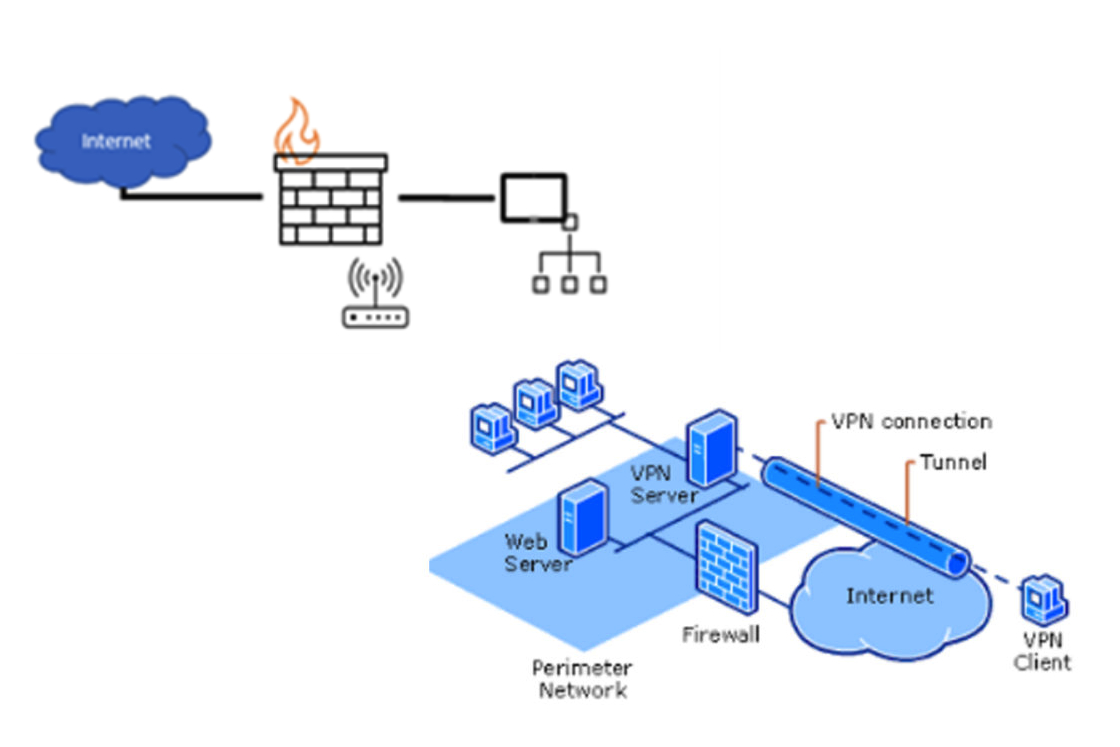
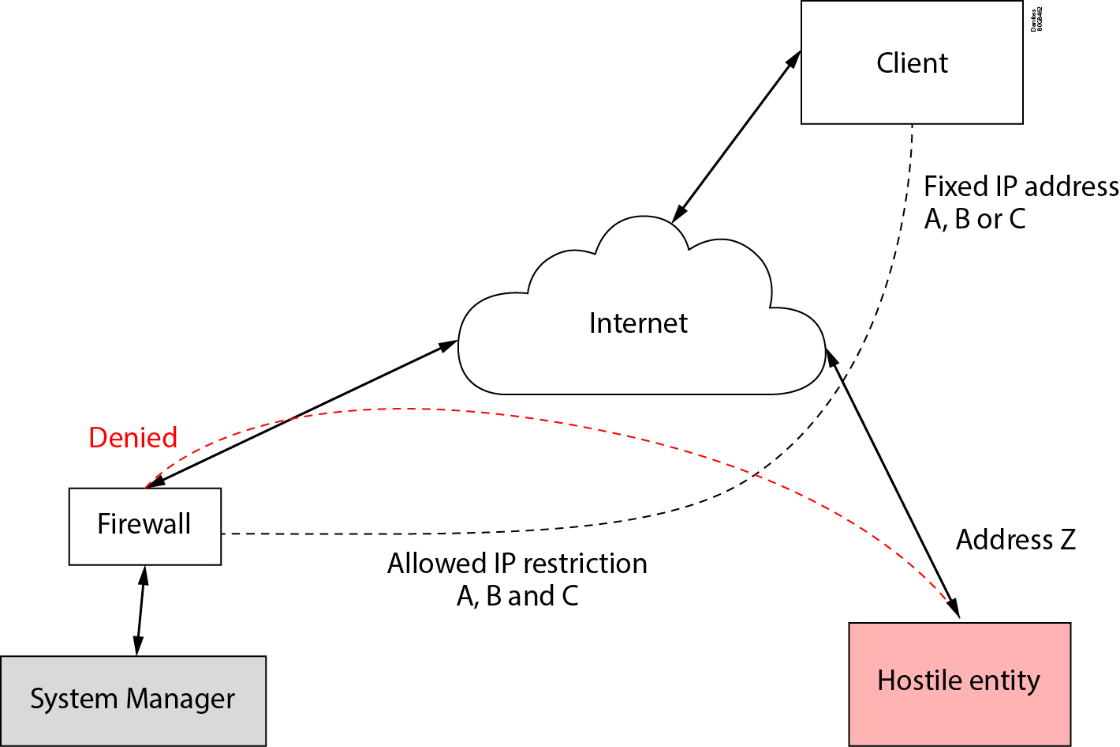
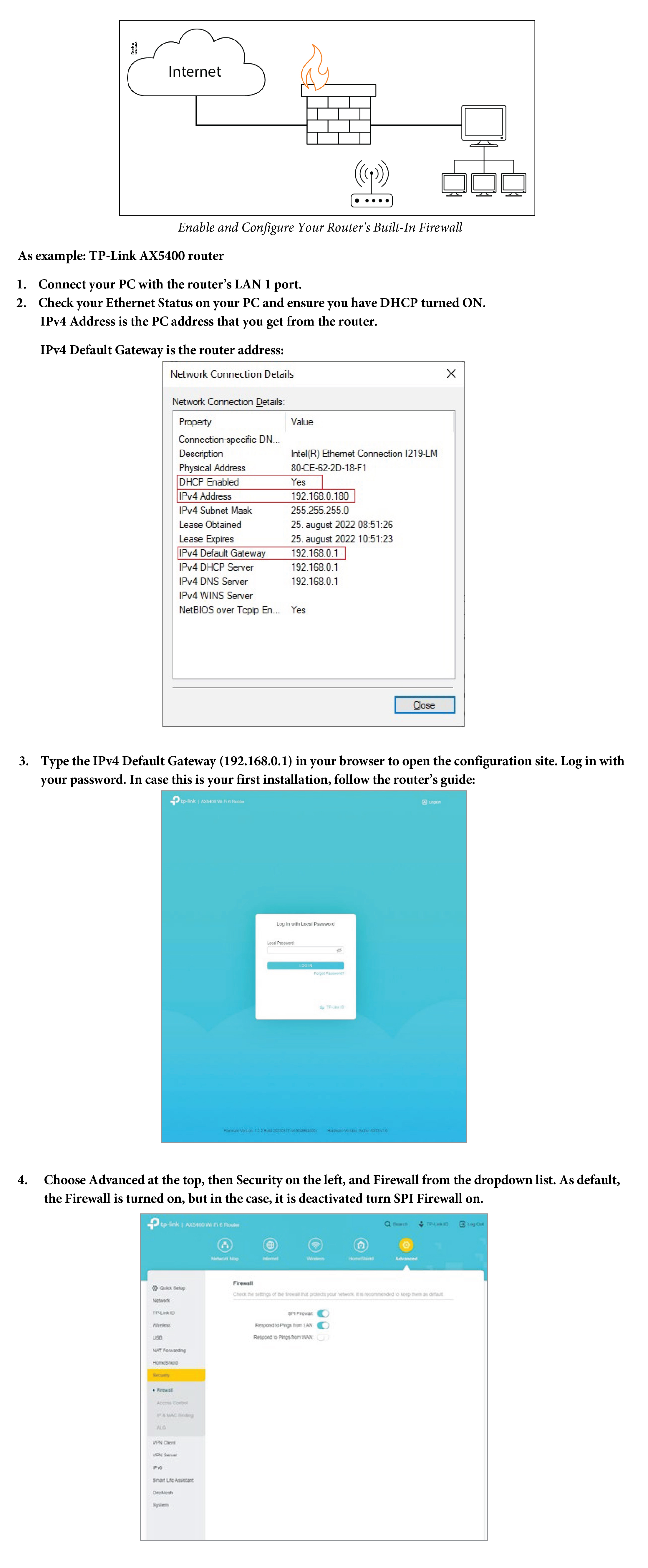
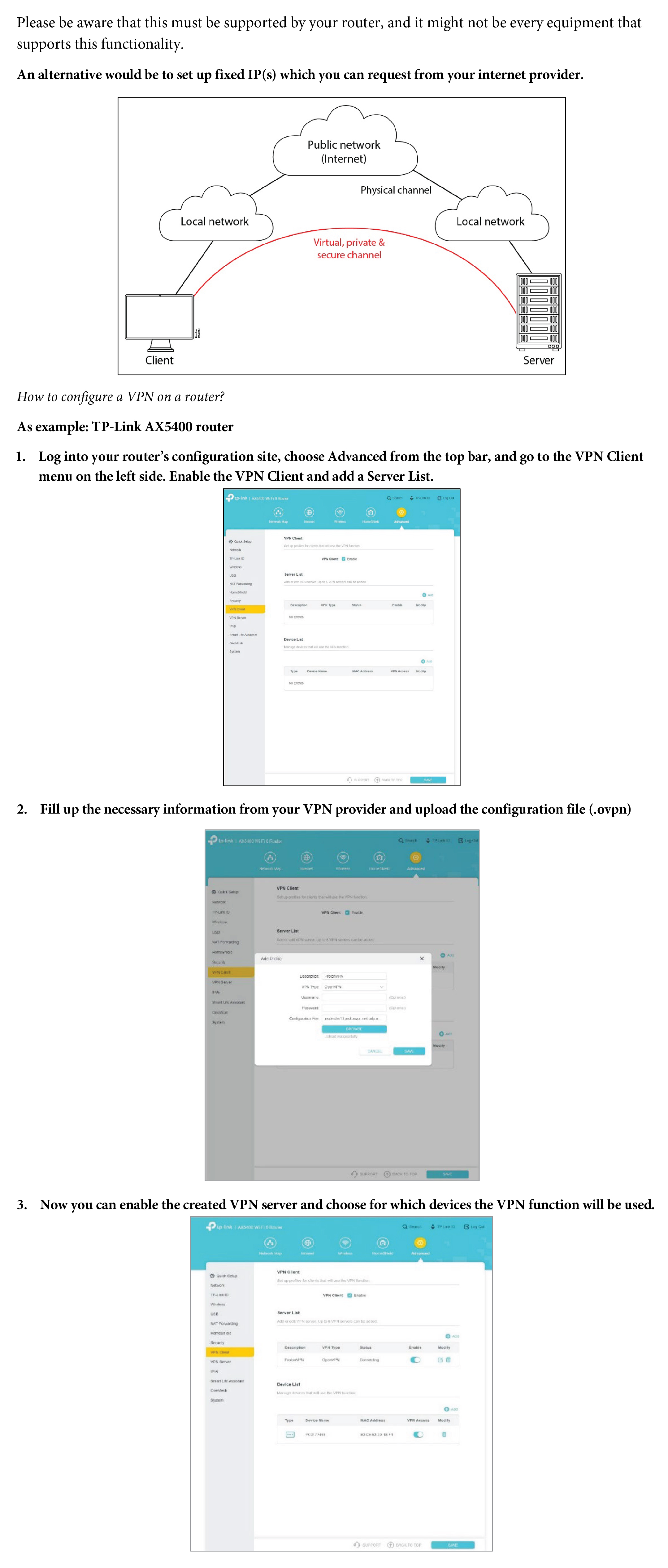
Danfoss strongly recommends protecting any network devices with a firewall and secure remote access principles.
The problem that may be experienced is that systems that are not fully updated may contain known remote exploits, that can have negative effects on the system. Known exploits are often published in the CVE databases, and on many security research sites.
This means that mapping the devices directly out on the internet is not recommended, but if it is necessary, it is important to use several safeguards to protect the system from direct internet access.
The general concerns for the devices are.
- DDOS – no software patches can protect against this kind of attack. (Thus, firewall protection is necessary)
- Known remote executions can allow an attacker to enter the device, therefore all software upgrades are necessary to remove known exploits.
- The exploiting of various known and unknown security vulnerabilities can cause system downtime.
General Information
Cybersecurity can only be efficient when everybody contributes to making the installation system secure.
As shown in above visualization in the family of IEC-62443 standards, it will require a shared effort and activity since security is a shared responsibility. As product supplier Danfoss aims to comply with IEC 62443-4-1 & IEC 62443-4-2.
It will additionally require responsibility and mitigation from System Integrator and Asset Owner.
Check the documentation for product-specific information
Danfoss provides detailed information with every product. Review the product guides on the website or those that accompany your products to find cybersecurity recommendations and best practices directly related to your Danfoss products.
|
Check also online specific information like the Danfoss FAQ page, where this best practice guide was placed. |
For additional information on cybersecurity best practices, review these resources:
- Quick Start Guide: An Overview of the ISA/IEC 62443 Series of Standards
ISA Global Cybersecurity Alliance (ISAGCA) - Cybersecurity Best Practices
Center for Internet Security - IEC 62443 Security for Industrial Automation and Control Systems
International Society of Automation (ISA)
Disclaimer:
THIS DOCUMENT IS INTENDED TO HELP PROVIDE GENERAL SECURITY RECOMMENDATIONS AND IS PROVIDED ON AN “AS-IS” BASIS WITHOUT WARRANTY OF ANY KIND. DANFOSS DISCLAIMS ALL WARRANTIES, EITHER EXPRESS OR IMPLIED, INCLUDING WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. IN NO EVENT SHALL DANFOSS BE LIABLE FOR ANY DAMAGES WHATSOEVER INCLUDING DIRECT, INDIRECT, INCIDENTAL, CONSEQUENTIAL, LOSS OF BUSINESS PROFITS OR SPECIAL DAMAGES, EVEN IF DANFOSS HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. THE USE OF THIS DOCUMENT, INFORMATION CONTAINED HEREIN, OR MATERIALS LINKED TO IT ARE AT YOUR OWN RISK. DANFOSS RESERVES THE RIGHT TO UPDATE OR CHANGE THIS DOCUMENT AT ANY TIME AND IN ITS SOLE DISCRETION.